SecurityVulnerability.io
Collect, Display, Alert.
The Cyber Security
Vulnerability Database
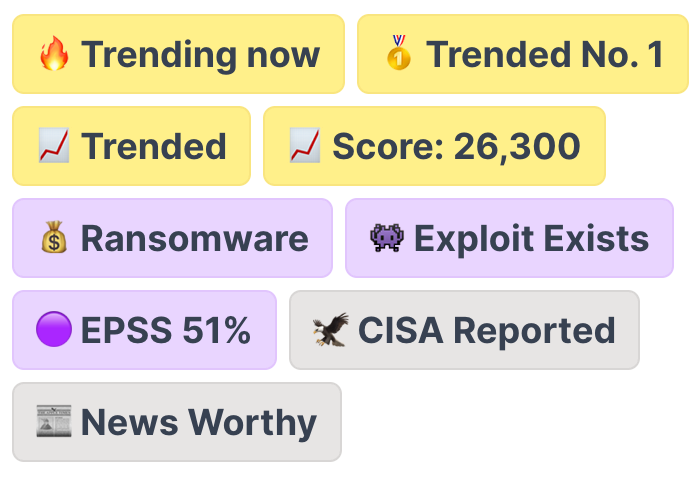
Trending
Vulnerabilities
If it's trending, then it's probably important.
Patch quicker!
Authentication Bypass in Cisco Catalyst SD-WAN Products
CVE-2026-20127
CiscoCisco Cataly...👾10CRITICAL
Elevation of Privilege Vulnerability in Windows Ancillary Function Driver by Microsoft
CVE-2026-21241
MicrosoftWindows 11 V...7HIGH
IP Address Bypass in Hono Web Application Framework Versions 4.12.0 and 4.12.1
CVE-2026-27700
HonojsHono8.2HIGH
Remote Code Execution Vulnerability in BeyondTrust Remote Support and Privileged Remote Access
CVE-2026-1731
BeyondtrustRemote Suppo...💰👾🟡🟣9.9CRITICAL
Latest Ransomware
Vulnerabilities
Command Injection Vulnerability in Privileged Remote Access and Remote Support Products
CVE-2024-12356BeyondtrustRemote Support📈💰👾🟡EPSS 93%🦅📰9.8CRITICALStack Buffer Overflow Vulnerability in OpenSSL Parsing CMS Messages
CVE-2025-15467OpenSSLOpenSSL💰👾🟡📰9.8CRITICALSecurity Control Bypass in SolarWinds Web Help Desk
CVE-2025-40536SolarwindsWeb Help Desk💰👾EPSS 66%🦅📰8.1HIGHRemote Code Execution Vulnerability Affects Microsoft Configuration Manager
CVE-2024-43468MicrosoftMicrosoft Configuratio...📈💰👾🟡EPSS 84%🦅📰9.8CRITICALRemote Code Execution Vulnerability in BeyondTrust Remote Support and Privileged Remote Access
CVE-2026-1731BeyondtrustRemote Support(rs) & P...🥇📈💰👾🟡EPSS 61%🦅9.9CRITICAL
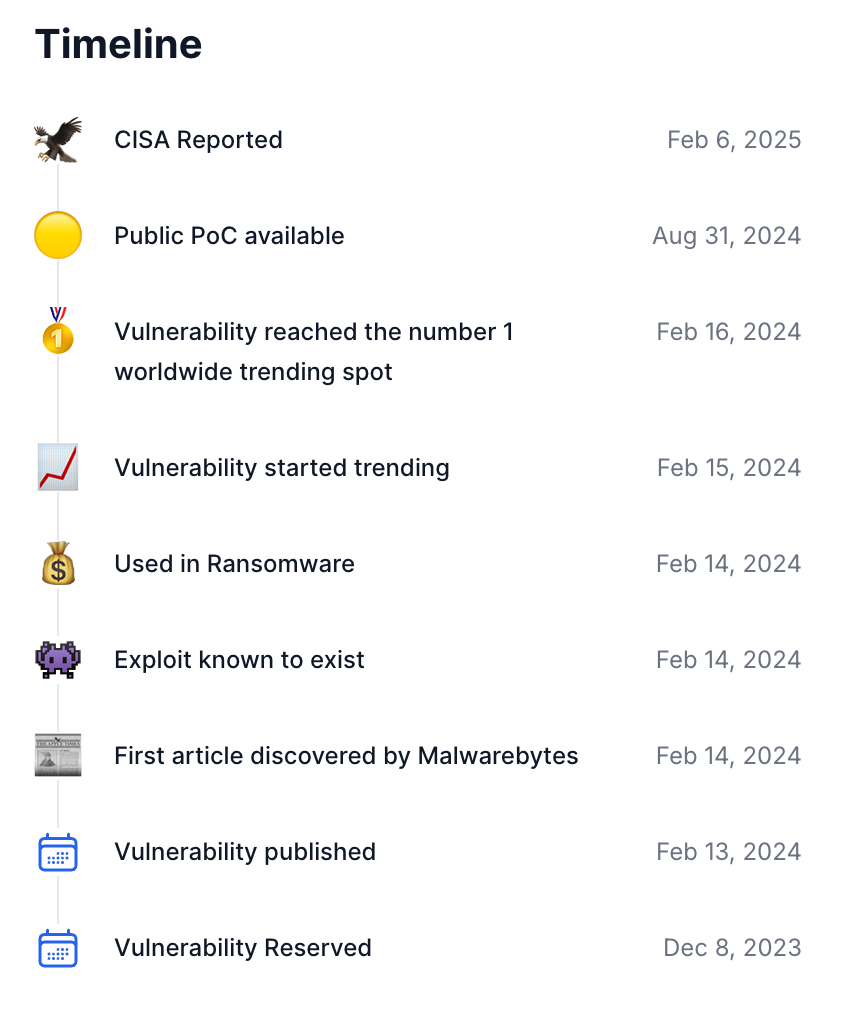
20 February 2026
19 February 2026
13 February 2026
Exploit Intelligence by SecurityVulnerability.io
Understand what's being exploited!
Highlighting what's important
Emerging vulnerabilities & threats
Every hour we analyze over 50 data sources to identify the emerging threats that matter to you, and your business!

Trusted by
SecurityVulnerability.io was built to help colleagues in the industry.
- Active Users
- 30k+
- Data Sources
- 50+
- Vulnerabilies Tracked
- 200k+
- New Vulnerabilities Each Day
- 120+
5 out of 5 stars
“Understanding what's really important in a world with too much information allows Cytadel to always be at the cutting edge of protective activites.”

Manit Sahib
CEO of Cytadel
Boost your productivity.
Start using SecurityVulnerability.io
The database is open and free to use.
Advanced queries and alerting require a free account.
Frequently asked questions
- 🔐 What is SecurityVulnerability.io?
- SecurityVulnerability.io is a live platform that curates, summarizes, and explains critical Cyber Security vulnerabilities (CVEs) for security professionals, engineers, and IT teams. We make it easier to track threats across vendors like Microsoft, Cisco, Apple, and more — without the noise.
- 🔍 How does SecurityVulnerability.io work?
- We analyze thousands of sources, including CVE databases, vendor advisories, and security blogs, to provide you with the most relevant and actionable information. Our platform uses advanced algorithms to filter out noise and highlight the vulnerabilities that matter most.
- 📅 How often is the site updated?
- We publish updates hourly. New CVEs, emerging exploits, high-severity alerts, and major vendor advisories are continuously monitored and posted.
- 🔔 How can I stay informed about new vulnerabilities?
- You can subscribe to our newsletter, follow us on social media, or set up alerts on our platform to receive notifications about new vulnerabilities and updates.
- 💰 Is SecurityVulnerability.io free?
- Yes! Our platform is completely free to use. We believe in providing valuable resources to the Cyber Security community without any cost.
- 🛠️ Do you provide exploit details or PoCs?
- When available and publicly disclosed, we include links to proof-of-concept (PoC) exploits, or tag the vulnerability as actively exploited in the wild. However, we never host code ourselves.